How To Hack A Coke Machine Youtube
How I hacked modern Vending Machines


"Striking and kicking" the arranged App of their widest European distribution company.
PREFACE
Indisputably, Vending Machines are objects of cult. Delicious morsels of Hackers, ever. In the beginning they worked offline with coins only, and so, NFC- keys/cards models started spreading. If I say "COGES" I'1000 sure that meliorate times will come up to someone'southward heed. But… In a bunch of years things changed radically. Yous distract and a moment later on, discover the world superseded by things connected to the internet…
STORY
One mean solar day I decided to interrupt seasoning myself in the bat-cave and direct to my hometown to get some sunlight, so I went to the University to salute an old professor.
"Go to have a coffee!" — he said— and we started chit-chatting while walking through the main corridor.
Once arrived…
Me: "allow me pay, I have coins!".Him: "await expect! let me apply the Vending Machine's App to pay, the coffee will exist cheaper".

BLE + NFC
Brain: "Mmm… Virtual wallets are cool stuff…".
Fantabulous.

HOT-POT
Soul: "I dare you to Hack into that!"

~$ White Chapeau inner vox: "only pats on the shoulder if no problems bounty reward". ~ $ Grey Hat inner vocalisation: "ok, I'll exercise that for educational purposes only". ~ $ Black Hat inner voice: "c'mon human being, let's spiral that HEAP, dandy Jupiter!".
Later in that day…

Pwnie limited.

Analysis
Needless to say that I picked up my dirty rooted Android smartphone (with USB Debugging Enabled), installed the targeted App from the Play Shop and dumped the original *.apk to my laptop via adb.
# adb pull /data/app/com.sitael.vending-1/base.apk ./Argenta.apk
I decompiled the *.apk with apktool
# apktool d ./Argenta.apk -o ./Argenta
and extracted Java sources with jadx
# jadx ./Argenta.apk
Firstly, I made the *.apk debuggable by editing the AndroidManifest.xml file by adding **android:debuggable="truthful"** property to the **application <tag>**
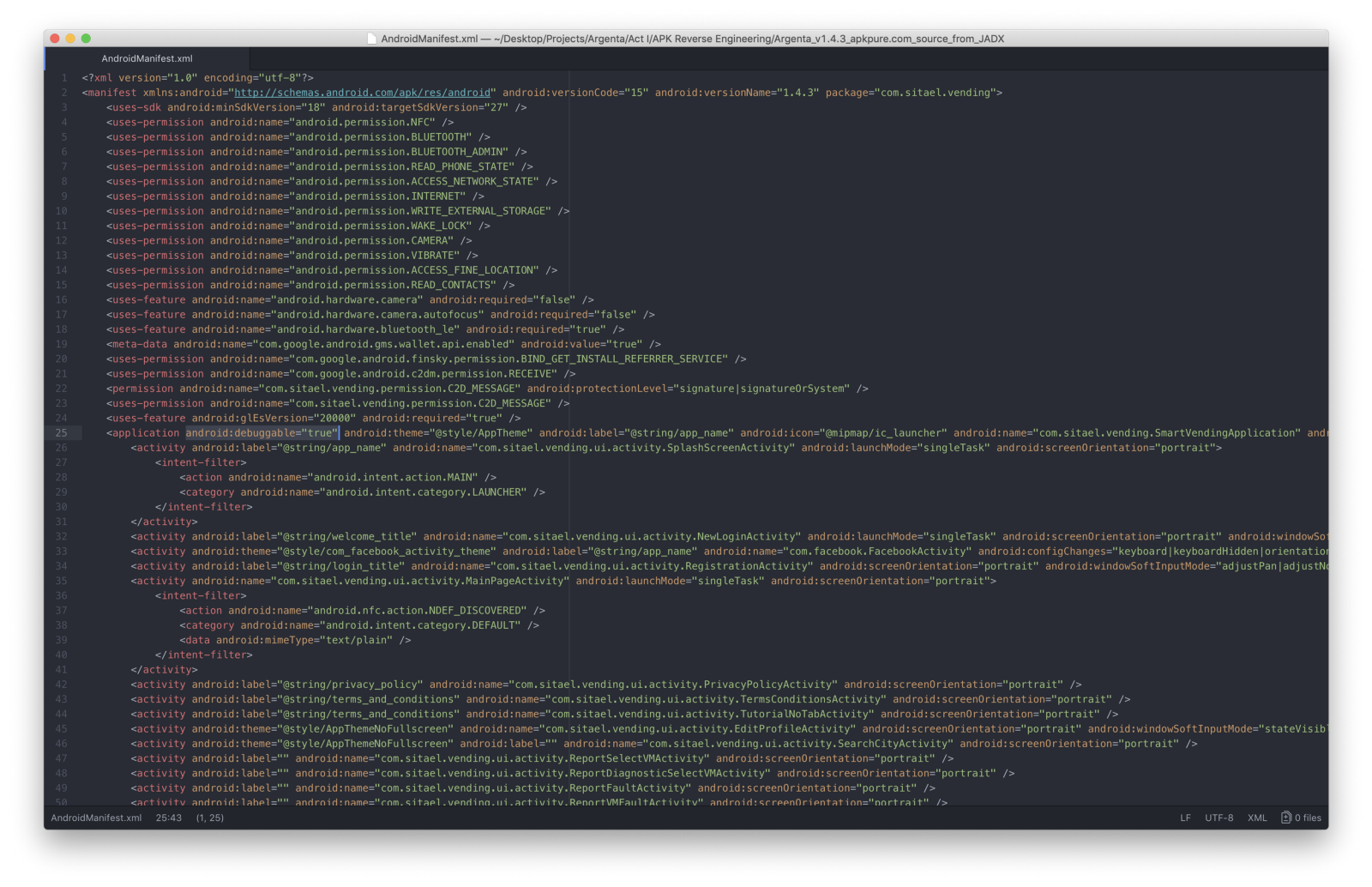
So, I rebuilt the *.apk
# apktool b ./Argenta
created a new key with keytool
# keytool -genkey -v -keystore Argenta.keystore -alias Argenta -keyalg RSA -keysize 2048 -validity 10000
signed the *.apk with jarsigner using the generated cardinal
# jarsigner -verbose -sigalg SHA1withRSA -digestalg SHA1 -keystore Argenta.keystore Argenta.apk Argenta
lastly, I zip-aligned it to make it runnable
# zipalign -v iv Argenta.apk Argenta-signed.apk
and I installed the terminal *.apk
# adb install ./Argenta-signed.apk
I ran the App on the smartphone and I started looking at logs with logcat by filtering them via its package proper name
# adb logcat --pid=`adb shell pidof -south com.sitael.vending`
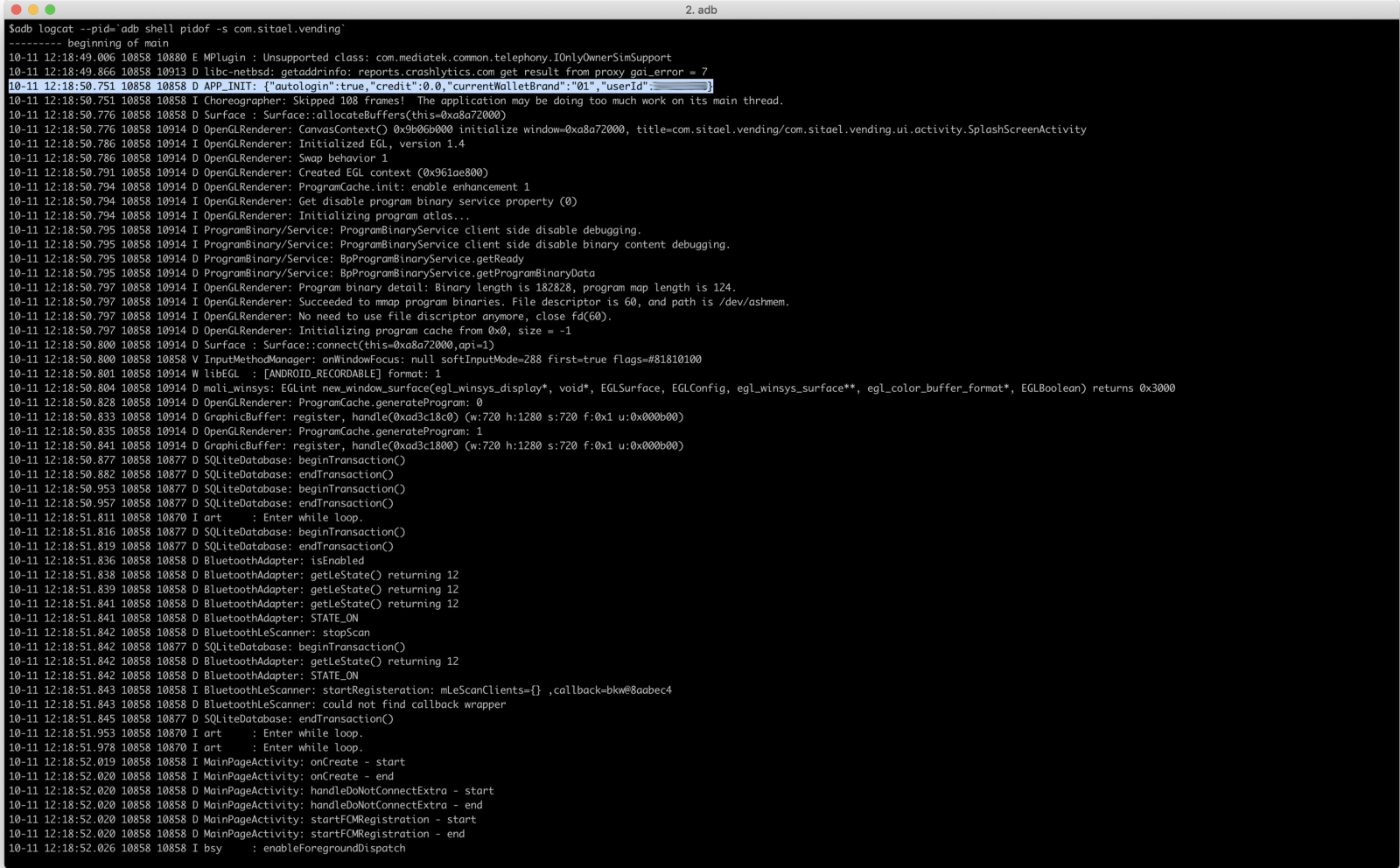
Aught special institute, so I started to rummage through the source codes seeking for juicy information.
Looking ameliorate at **AndroidManifest.xml** file, I constitute references to RushOrm
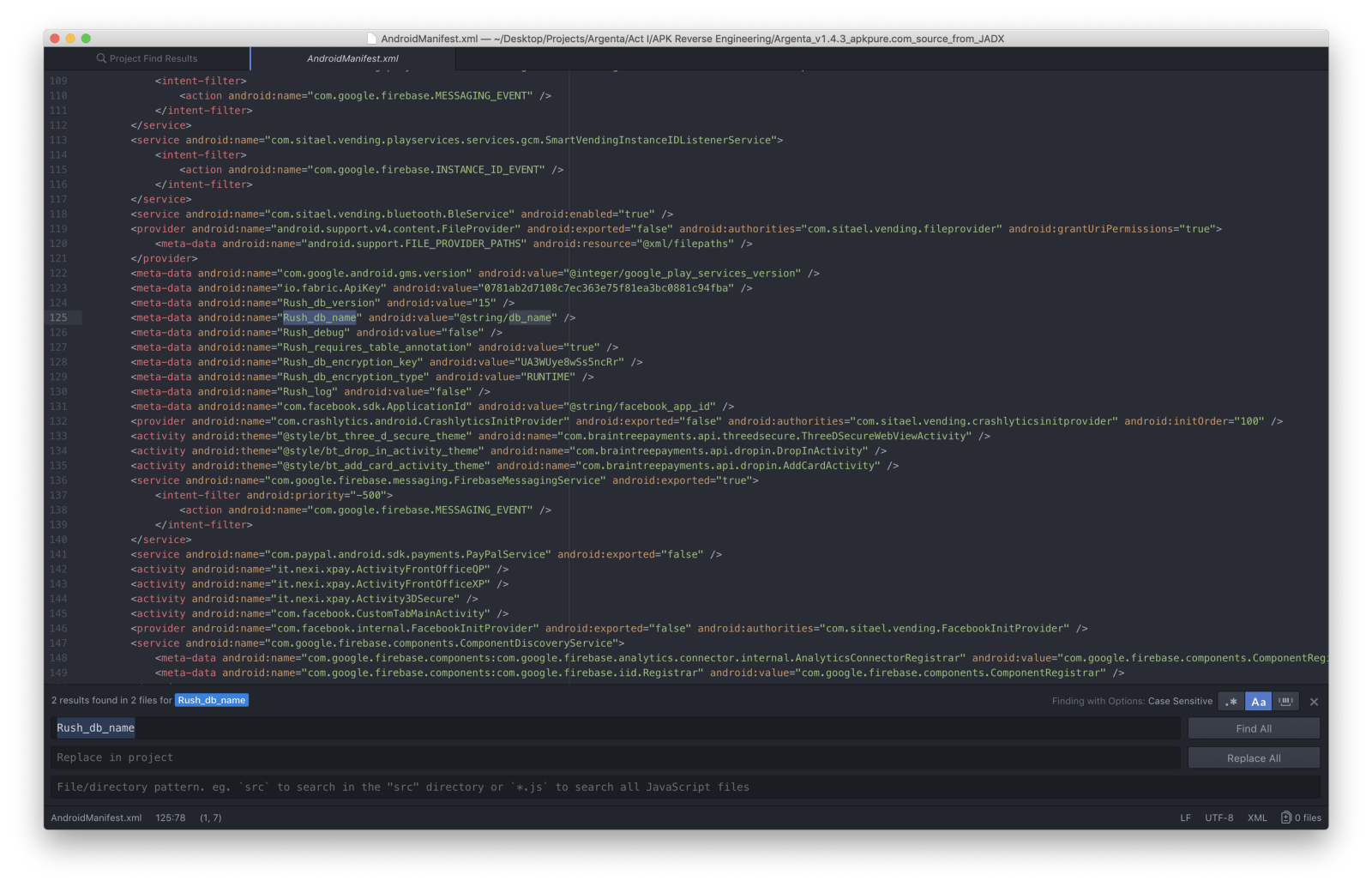
And then, first keyword search was **db_name**
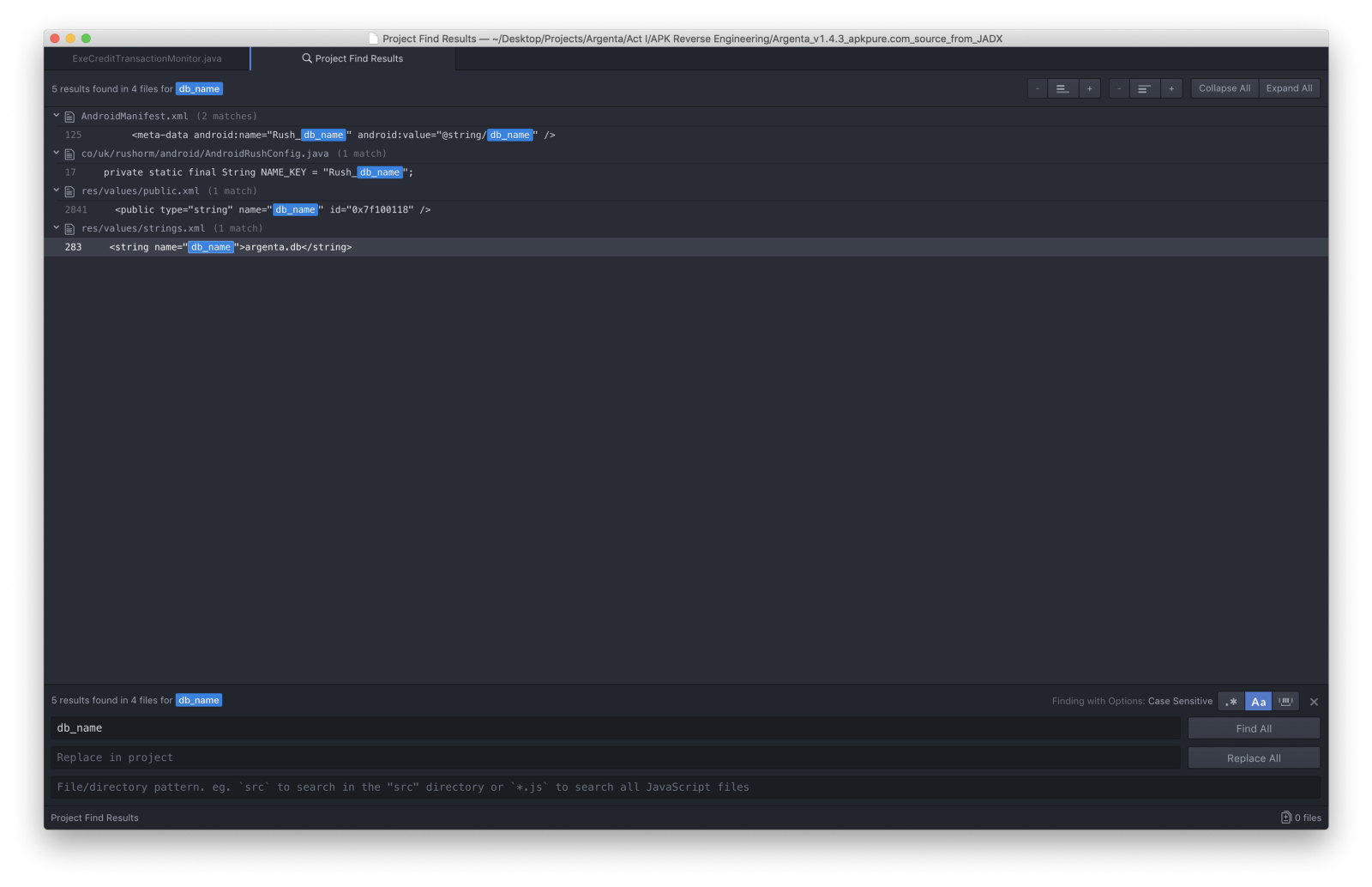
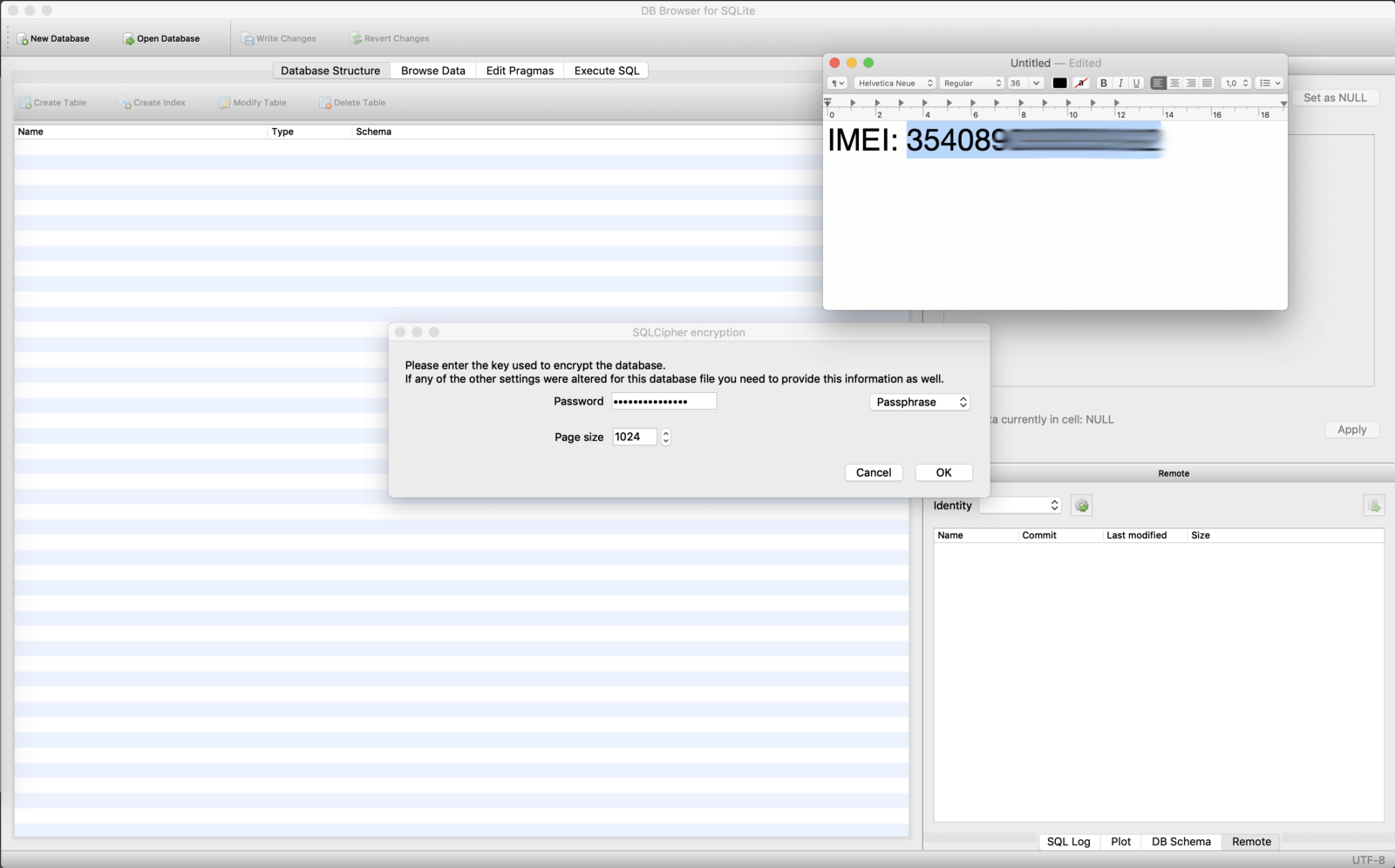
Cool. I booted upward the Root Explorer on the telephone seeking for **argenta.db**
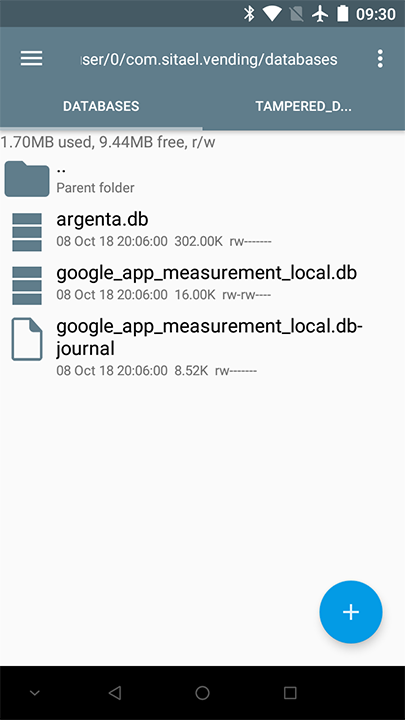
Establish. And so I pulled information technology to my laptop with adb
# adb pull /information/data/com.sitael.vending/databases/argenta.db ./
and tried to open information technology with a DB Browser for SQLite
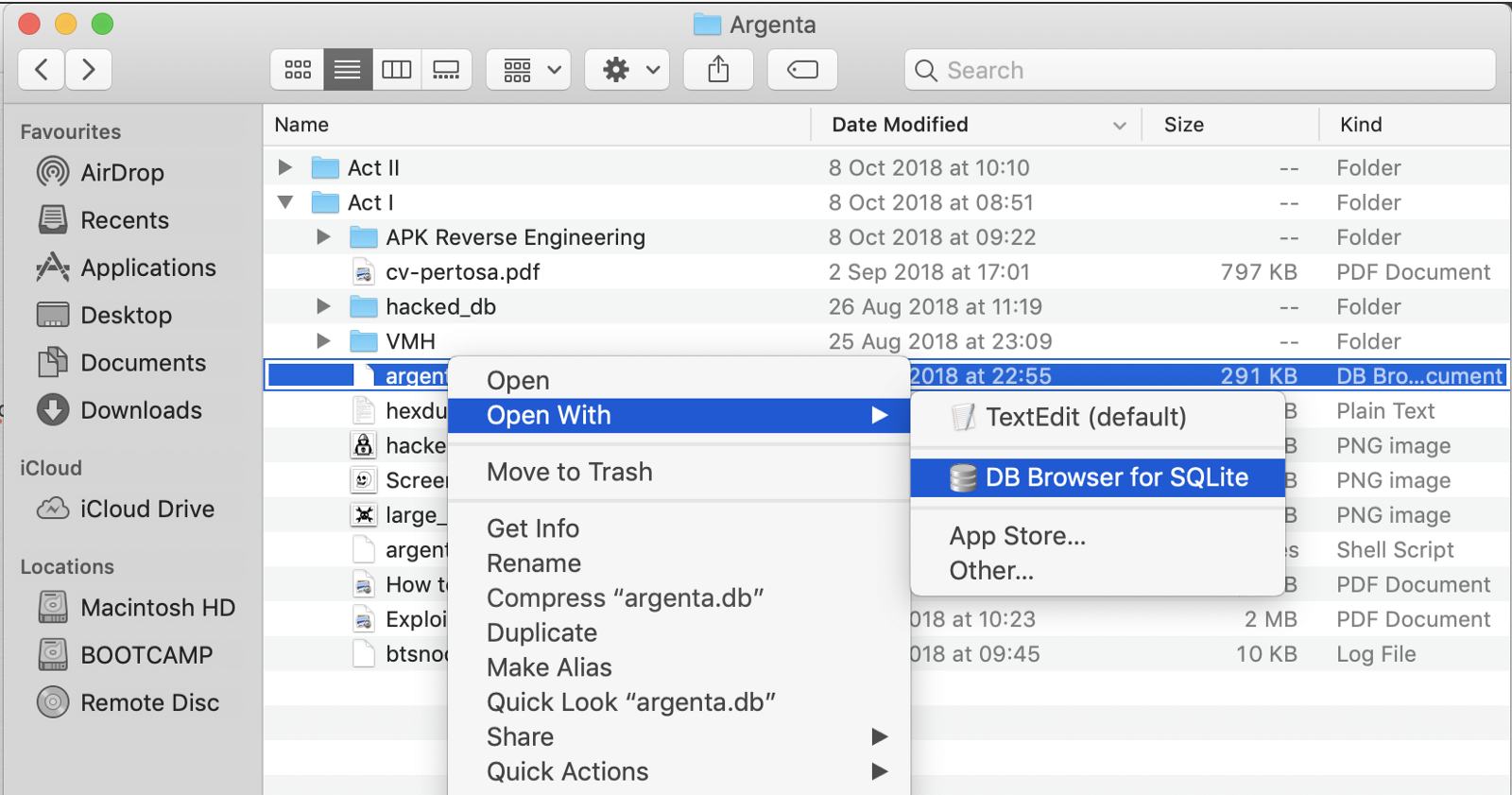
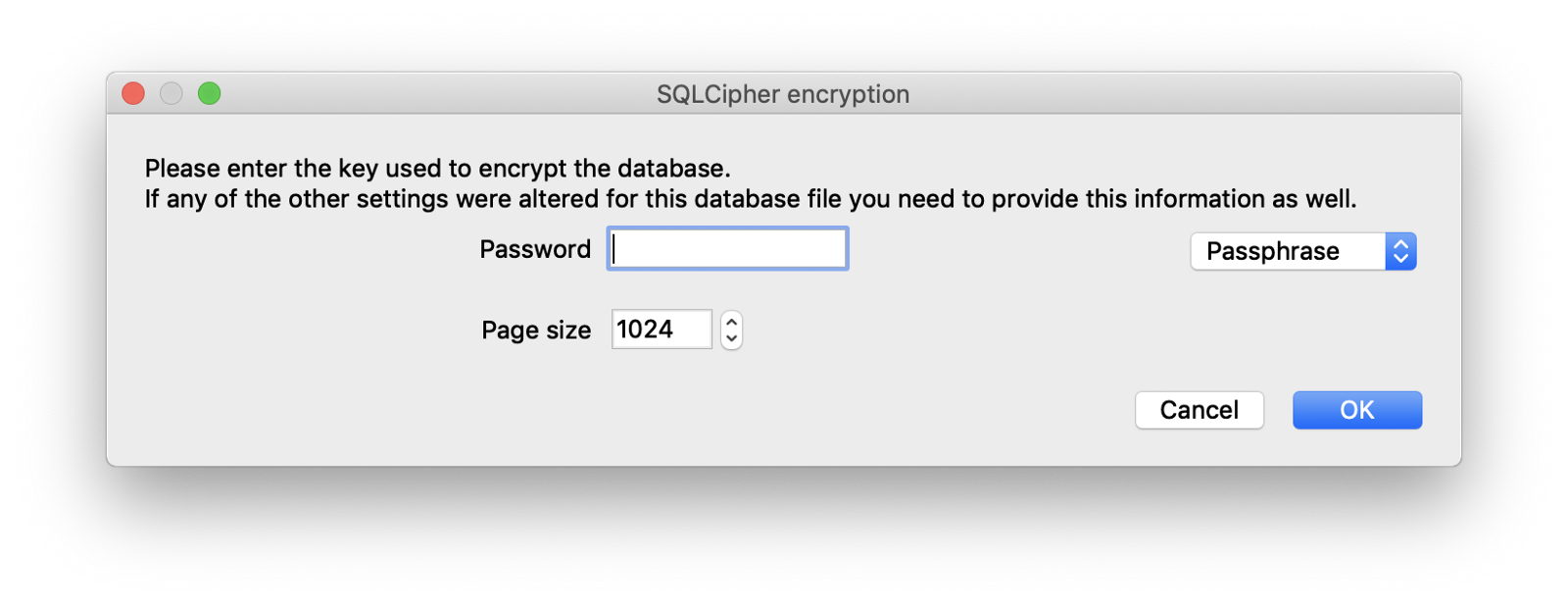
obviously, it was password protected
REVERSE-Applied science
Pace back to the source codes, looked at **RushAndroidConfig.coffee**
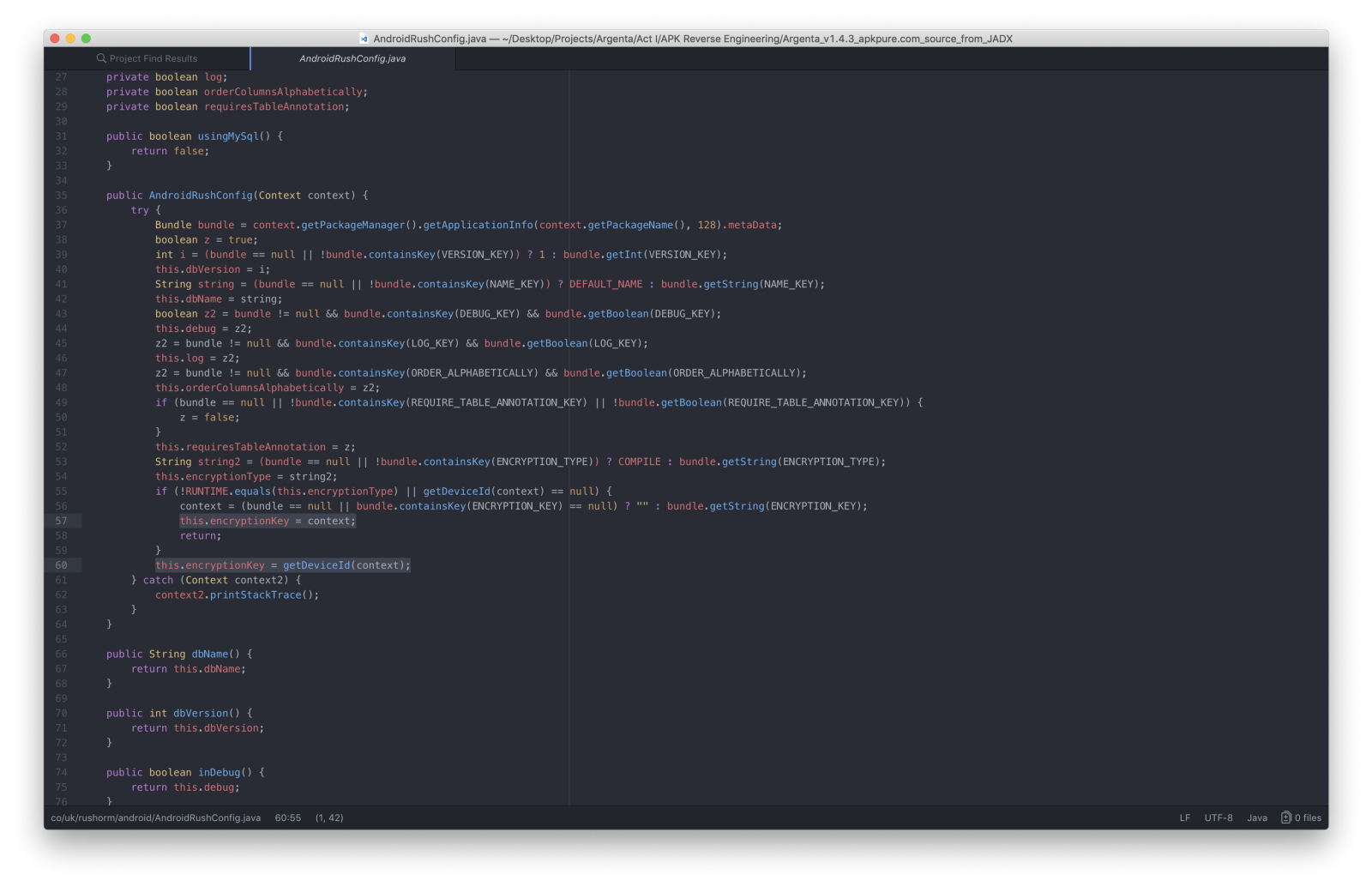
where I plant the methods used to configure the database.My attending was caught by **this.encryptionKey = getDeviceId(context);**
I moved to its definition and…
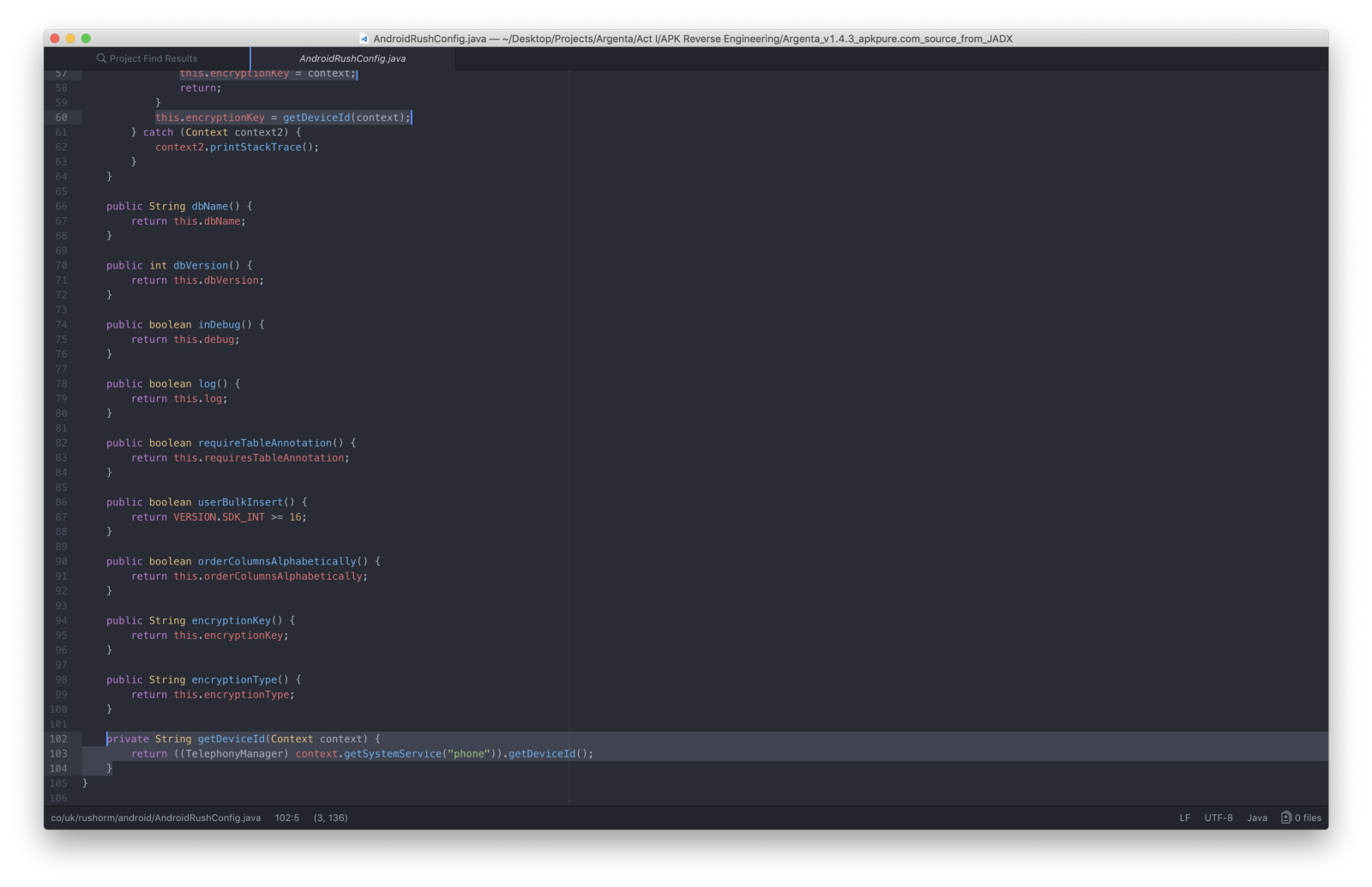
Establish that the targeted App used the phone's IMEI **(*#06#)**as encryption primal for the SQLite database.
Alchemy.
Boom baby.

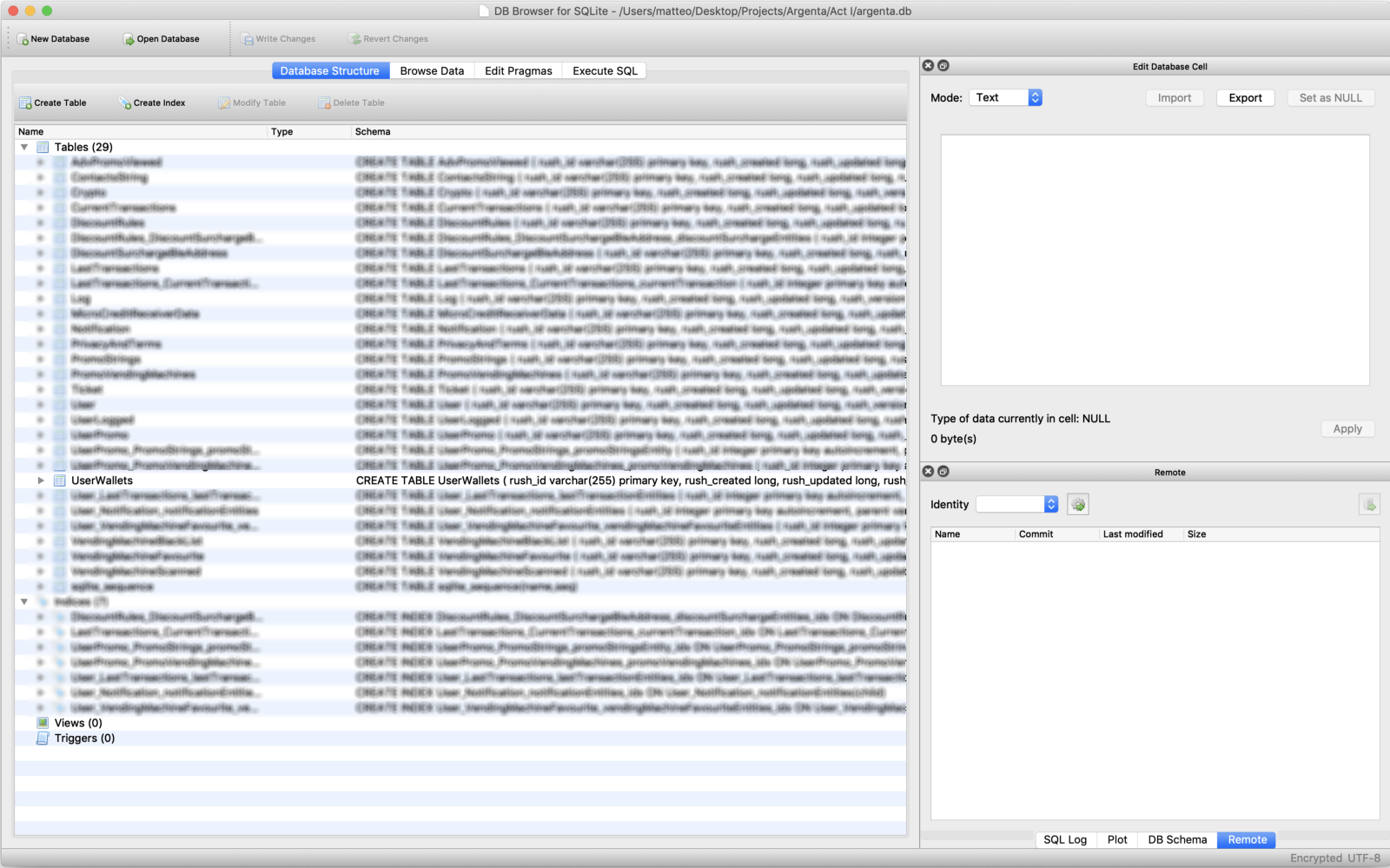
After a couple of seconds of inspection, I opened to the **UserWallets** table

and edited the **walletCredit** field writing changes

so I pushed the database with pumped credit back to the phone
# adb pull ./argenta.db /data/data/com.sitael.vending/databases/argenta.db
VERDICT
In the meantime, while I felt like "Robin Hood" (nostalgic and explicit reference to Age Of Empires crook code for +1000 gold) I adult an Android utility to quickly dump/restore/tamper the targeted App'due south database on the fly.
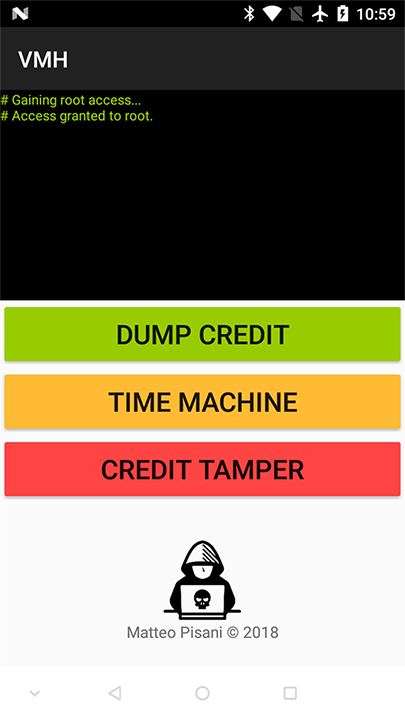
then I went back to my University over again to finally test the Hack
Honey diary…

Conclusion
From zilch-credit business relationship, I could:
> Inflate the App's credit.> Buy stuff.> Go the remaining credit updated.> Become back to zero-credit country.> Inflate the credit again.> Start over.
With a macro inspection of all the reversed sources I found huge portion of make clean lawmaking — without obfuscation — that meant no great counter-measures adopted to protect user data and make the App secure at all.
A month ago…
The White Lid inner vocalization of me picked upwards the telephone and called the company behind this shame to written report the vulnerability. I gently suggested them to toss the current architecture and develop a better and secure one from scratch.
Hocus bogus.

Cybersecurity Writing Contest
"Hitting and kicking" the bundled App of their widest European distribution company.
PREFACE
Indisputably, Vending Machines are objects of cult. Delicious morsels of Hackers, always. In the get-go they worked offline with coins only, then, NFC- keys/cards models started spreading. If I say "COGES" I'm sure that better times will come to someone's listen. But… In a agglomeration of years things changed radically. You distract and a moment after, find the world superseded past things continued to the internet…
STORY
One twenty-four hour period I decided to interrupt seasoning myself in the bat-cave and direct to my hometown to get some sunlight, so I went to the University to salute an quondam professor.
"Go to have a java!" — he said— and we started chit-chatting while walking through the main corridor.
Once arrived…
Me: "let me pay, I have coins!".Him: "expect expect! let me use the Vending Machine'due south App to pay, the coffee will be cheaper".

BLE + NFC
Brain: "Mmm… Virtual wallets are cool stuff…".
Excellent.

HOT-POT
Soul: "I dare y'all to Hack into that!"

~$ White Lid inner vocalization: "just pats on the shoulder if no bug bounty reward". ~ $ Grey Chapeau inner voice: "ok, I'll do that for educational purposes only". ~ $ Black Hat inner phonation: "c'mon man, let's screw that HEAP, smashing Jupiter!".
Afterwards in that twenty-four hour period…

Pwnie express.

ANALYSIS
Needless to say that I picked up my dirty rooted Android smartphone (with USB Debugging Enabled), installed the targeted App from the Play Shop and dumped the original *.apk to my laptop via adb.
# adb pull /data/app/com.sitael.vending-ane/base of operations.apk ./Argenta.apk
I decompiled the *.apk with apktool
# apktool d ./Argenta.apk -o ./Argenta
and extracted Java sources with jadx
# jadx ./Argenta.apk
Firstly, I made the *.apk debuggable past editing the AndroidManifest.xml file by adding **android:debuggable="true"** property to the **application <tag>**

Then, I rebuilt the *.apk
# apktool b ./Argenta
created a new key with keytool
# keytool -genkey -v -keystore Argenta.keystore -alias Argenta -keyalg RSA -keysize 2048 -validity 10000
signed the *.apk with jarsigner using the generated primal
# jarsigner -verbose -sigalg SHA1withRSA -digestalg SHA1 -keystore Argenta.keystore Argenta.apk Argenta
lastly, I zip-aligned information technology to brand it runnable
# zipalign -v 4 Argenta.apk Argenta-signed.apk
and I installed the final *.apk
# adb install ./Argenta-signed.apk
I ran the App on the smartphone and I started looking at logs with logcat by filtering them via its package name
# adb logcat --pid=`adb beat out pidof -southward com.sitael.vending`

Nothing special found, so I started to comb through the source codes seeking for juicy information.
Looking ameliorate at **AndroidManifest.xml** file, I found references to RushOrm

So, kickoff keyword search was **db_name**

Cool. I booted up the Root Explorer on the phone seeking for **argenta.db**

Found. So I pulled information technology to my laptop with adb
# adb pull /information/data/com.sitael.vending/databases/argenta.db ./
and tried to open it with a DB Browser for SQLite

manifestly, it was password protected

Reverse-ENGINEERING
Stride dorsum to the source codes, looked at **RushAndroidConfig.java**

where I establish the methods used to configure the database.My attention was caught by **this.encryptionKey = getDeviceId(context);**
I moved to its definition and…

Found that the targeted App used the phone's IMEI **(*#06#)**every bit encryption key for the SQLite database.
Abracadabra.

Boom baby.


After a couple of seconds of inspection, I opened to the **UserWallets** table

and edited the **walletCredit** field writing changes

then I pushed the database with pumped credit back to the phone
# adb pull ./argenta.db /data/information/com.sitael.vending/databases/argenta.db
VERDICT
In the meantime, while I felt similar "Robin Hood" (nostalgic and explicit reference to Age Of Empires crook code for +1000 gold) I developed an Android utility to quickly dump/restore/tamper the targeted App's database on the wing.

and so I went back to my University over again to finally test the Hack
Dear diary…

CONCLUSION
From zip-credit account, I could:
> Inflate the App's credit.> Purchase stuff.> Become the remaining credit updated.> Go dorsum to zero-credit country.> Inflate the credit once more.> Starting time over.
With a macro inspection of all the reversed sources I found huge portion of clean code — without obfuscation — that meant no keen counter-measures adopted to protect user information and make the App secure at all.
A month ago…
The White Chapeau inner vocalism of me picked upward the telephone and chosen the company behind this shame to report the vulnerability. I gently suggested them to toss the electric current architecture and develop a better and secure one from scratch.
Hocus bogus.

Tags
Related Stories
Source: https://hackernoon.com/how-i-hacked-modern-vending-machines-43f4ae8decec
Posted by: pappalardoyouten.blogspot.com

0 Response to "How To Hack A Coke Machine Youtube"
Post a Comment